Incognito CTF 4.0
Web
Get flag 1
SSRF ?url=http://0.0.0.0:9001/flag.txt
Low on options
根據題目提示用OPTIONS request得到As I said, I am low on options...。 一句廢話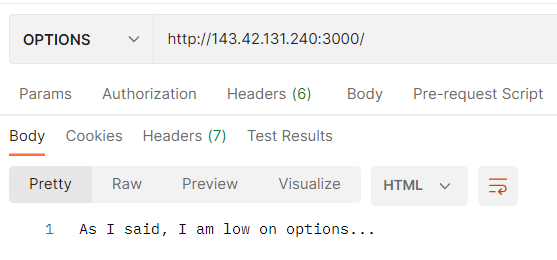
索性把所有method全部試一次,PROPFIND request拿到flag。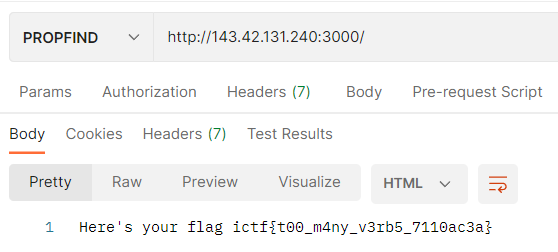
Crypto
Ancient
拿到一個缺header的png檔,將header補上後得到有象形文字的圖片,以圖搜圖查到是十三世紀的一種記數方式,用此網站轉成數字對照Ascii table便可拿到flag。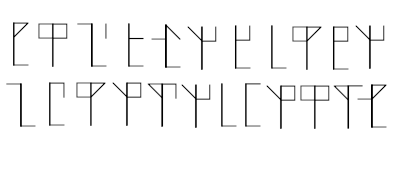
Pyjail
The only jail
nc進去發現是一個偽裝過的Python環境,有過濾一些像斜線、反斜線、大括號等字元,用os的path join便可湊出路徑用讀取flag。
1 | Welcome to the IIITL Jail! Escape if you can |
Rev
Meow
flag藏在.rodata
Pwn
Baby Flow
checksec什麼都沒開,BOF把return address置換成get_shell的即可。
1 | from pwn import * |